All Together Now:
Don't Store What You Don't Need
 t's only April, but 2005 is already a big year for identity theft news, which seems to have reached epidemic proportions. Criminals stole data from 145,000 ChoicePoint records in October 2004, but the company didn't announce the breach until February 2005, nearly four months later, when it began to notify consumers that their information might have been compromised. t's only April, but 2005 is already a big year for identity theft news, which seems to have reached epidemic proportions. Criminals stole data from 145,000 ChoicePoint records in October 2004, but the company didn't announce the breach until February 2005, nearly four months later, when it began to notify consumers that their information might have been compromised.
And in March, intruders gained access to log-in and password information for 32,000 LexisNexis subscribers. DSW Inc., a shoe retailer and division of Retail Ventures Inc., said that account data for purchases made in 103 of its 175 stores had been stolen.
Bank of America Corp. (BofA) announced it misplaced data tapes containing information on more than 1 million federal employees.
BofA is also the subject of a lawsuit filed in Florida in March, in which a small-business owner is demanding reimbursement because the bank let an unauthorized wire transfer from the businessman's account go through to a bank in Latvia. (See related story on page 93 of this issue.)
When it comes to identity theft, the numbers are so big and the issues so vast that the problem is almost incomprehensible. Nearly 10 million Americans had their identities stolen last year, according to Federal Trade Commission (FTC) and Better Business Bureau estimates; in 2003, consumers suffered losses of $5 billion and businesses lost nearly $50 billion.
In the end, it boils down to individual consumers and the choices they make in the marketplace: With enough cause for concern, they might decide that the convenience of shopping and banking online isn't worth the risk of falling victim to identity theft.
If it happens often enough, consumers might decide that paying with cash isn't such a bad idea after all.
Two reports published recently by research and analysis firm Financial Insights (FI) support these notions. One showed that despite a record-breaking holiday season and year-in-total for e-commerce, more than 18% of consumers (or 40 million people) have stopped shopping online. The other reported that 6% of bank customers (or 12 million people) have switched banks to protect their assets.
When businesses in financial services can ensure the viability of the payment system, consumers will feel confident about using it. What can the payments industry learn from hacks made into the information storage systems of data brokers?
All Data Deserve Equal Protection
With all the recent bad news, at least people are now talking about information security and how it's protected in the payments industry. In the evolutionary process of creating a secure system, awareness is vital.
ChoicePoint, LexisNexis, BofA, and DSW shoe stores, along with last year's hack into BJ's Warehouse system, have all brought the reality of personal and financial information theft to light.
However, these cases involve different types of stolen data: ChoicePoint and LexisNexis are data aggregators and brokers, not merchants or credit card brands. Is it relevant to compare them?
Some people in the financial services industry insist that consumer data collection companies are distinct from financial institutions by nature of what they do and how they're regulated.
Many people had probably never heard of ChoicePoint before the news story hit in February. Some were probably not aware that companies like ChoicePoint make a lot of money filling their databases with personal consumer information, that they then sell to such companies as insurance carriers, lenders and financial institutions for marketing purposes.
Most consumers know that they should check credit card statements for unauthorized purchases and review credit reports regularly. Most people don't know how many different parties are involved in every transaction made with a payment card.
The fact remains that people lump all reports of stolen personal data together and reports of large-scale identity theft, no matter the source, make them question the safety of their own information.
"At a high level, these issues are related," said Michael Petitti, Senior Vice President at Ambiron, a data security and compliance services firm in Chicago. "It's about the theft of personal information. The definition of personal or sensitive information may vary according to industry, but the bottom line is how the consumer views this issue."
Chris Noell, Vice President of Business Development for Solutionary Inc., a provider of managed IT security and risk assessment services with headquarters in Omaha, Neb., agreed.
He said that even though financial services companies are regulated differently than data collection corporations, the point of protecting consumer information is the same.
"ChoicePoint is a data aggregator that keeps information about individuals that needs to be protected," he said. "It's a key part of their identities, and it was exposed in this breach."
Noell believes there is an exact parallel to draw between ChoicePoint and consequences for merchants if they experience a security breach.
"If you put a merchant in the place of ChoicePoint, how does the scenario change? The type of data is slightly different, but there are still the same types of obligations and implications.
"Merchants aren't actively selling their account databases or cardholder information. But in terms of an information security breach, you have to consider what type of data you have, and what are the implications in storing them," Noell said.
Who Foots the Bill?
Assigning responsibility and fines for security breaches can lead to murky territory.
When BJ's system was compromised last year, card issuers sued the chain for $16 million to cover losses and the expense of reissuing tens of thousands of potentially compromised credit cards. BJ's in turn, filed suit against IBM for providing faulty software and wants $16 million in damages.
The FTC investigates security breaches under authority of the Gramm-Leach-Bliley Act, which includes provisions to protect consumers' personal financial information held by financial institutions. When breaches occur, the FTC looks for misrepresentations in merchants' claims about the level of security they provide to consumers.
Several recent FTC settlements showed that behind-the-scenes providers, including payment gateways and shopping carts, are implicitly bound, as the merchant is, to keep consumer data safe from unauthorized access.
Who foots the bill to cover losses? "Certainly there's the brand component involved, but when liability for theft of sensitive data is assigned, it is often assigned to the underwriter, typically an acquirer or an ISO," Petitti said.
"Acquirers do the majority of merchant underwriting, and they're the ones who are liable for any fines that come from the Associations or losses that may have to be reimbursed for fraudulent purchases."
When acquirers are dinged, they turn to the merchant for repayment.
Gathering better information during the merchant application process, similar to the "know your customer" policies banks enforce, will help identify high risk accounts and mitigate them before they become fraudulent situations.
However, "the card Associations can develop and market regulations, but the burden is on the acquirers to push merchants and service providers to adopt enhanced data security policies and procedures," Petitti said.
Ambiron has seen an increasing number of the acquirers it works with, such as Discover Financial Services and Paymentech LP, taking a more aggressive approach to educating merchants and promoting compliance.
Humboldt Merchant Services (HMS), an ISO and processor in Eureka, Calif. with 15,000 accounts nationwide, decided that being very proactive about educating its merchants makes preventative sense. Linda Grimm, Senior Vice President of Operations, said that facing greater liability, including fines to cover costs for reissuing compromised cards (up to $35 per card) is a big motivator.
HMS merchants receive compliance brochures with every welcome kit detailing Association programs, requirements and responsibilities. HMS provides even more detailed compliance information on its Web site, including charts explaining merchant levels and their associated compliance requirements.
Setting Regulations, Driving Behavior
Collaborative solutions for securing sensitive information are obvious answers to preventing data theft, but that will require cross-industry cooperation. In a report published in March 2005, FI analyst Sophie Louvel acknowledged that while there is a need for sharing data across commerce, the amount of data made available has to be controlled.
Additionally, any business that bases customer worthiness on personal financial criteria must implement improved fraud prevention measures.
"Although security at these data brokers must be enhanced, the larger task resides with all U.S. businesses that service customers to ensure that this stolen information is not used to compromise identities and commit fraud," Louvel wrote. "Achieving this goal requires a technology and organizational infrastructure for cooperation between businesses across industries."
That means learning from others' mistakes, as well as employing the precautions that work elsewhere.
Sen. Dianne Feinstein has sponsored a national version of the California law (SB 1386, which protects personal information collected by institutions) requiring companies to notify consumers in the event of a database hack.
"It's gaining support from industry members who would rather have a notification provision than other alternatives being discussed," Noell said. "Compared to facing regulatory consequences, living up to a good standard and having to notify customers is the lesser of two evils."
The proposed legislation would have implications for everyone in payments, including merchants.
Petitti said especially in payments, an industry that touches and affects so many others, including retail, petroleum and services, mitigation is imperative.
Establishing a philosophy for the standardization of protecting data is necessary from the brand component outward. "Everyone has a stake in it," he said.
John Shaughnessy, Senior Vice President of Fraud Control and Operations with Visa U.S.A., agreed. "Security is not just a Visa issue," he said. "It's bigger than Visa. It's a payment card industry issue that we all need to participate in."
Protecting consumer data and the security environment has been a high priority for Visa since 1998, Shaughnessy said. The Association has been instrumental in leading such collaborative initiatives as the Payment Card Industry Data Security Standard, or PCI.
This new standard, implemented in December 2004, is the alignment of Visa's Cardholder Information Security Program (CISP) and MasterCard International's Site Data Protection (SDP) program. It simplifies the process of compliance with security regulations. (See "PCI: Card Associations Unite to Fight Fraud With Collaborative Standard," The Green Sheet, Feb. 14, 2005, issue 05:02:01.)
Shaughnessy said that while CISP remains intact, having PCI in place means anyone who touches cardholder data now only needs to go through one assessment, instead of one for each card company. (Other brands have endorsed PCI and are expected to adopt the standard.)
Shaughnessy and Visa both participate in several industry-wide forums, including a panel discussion at the 2005 Electronic Transactions Association's (ETA) Annual Meeting and Expo on protecting cardholder data, and an "industry group" that has met regularly for over a year to talk about key issues.
"We need to be talking as an industry, not as brands, about environments, issues we're seeing and how we're trying to address those individually and collectively," he said.
Visa has made its concern over the highly sensitive information contained on the magnetic stripes of credit and debit cards a top priority. In fact, Shaughnessy called the elimination of mag stripe data from merchants' systems one of the Association's biggest imperatives right now. "We are focused on it like a laser," he said.
"Despite strict operating regulations from Visa that say you can't store the full content of the mag stripe, we've discovered in the last year or two that merchants and third parties are storing this information."
Full track (Track 1 and Track 2) data include a lot of sensitive information, said Ingrid Beierly, Visa's Director of CISP. This can include names, account numbers, expiration dates, service codes, Visa reserve value and card verification value (CVV) information.
Shaughnessy hopes the mag stripe content issue will also become a high priority for other card brands, issuers, processors, equipment manufacturers, software developers that enable the storage function and the merchants that request it. "Everyone needs to contribute," he said.
Of particular importance, Shaughnessy said, is protecting the CVV, a critical point in the authentication and authorization process.
Beierly investigates occurrences of fraud, conducting forensic analyses and working with law enforcement on hacking incidents and issues. Her investigations showed that software applications were inadvertently storing the critical CVV, and not destroying it following transaction authorizations.
Beginning in June 2004, she met with the top 25 software vendors. Following those talks, she prepared a list of best practices and distributed it to the providers. From those meetings came Visa's new CISP Payment Application Best Practices program.
The software standard provides security requirements for developers writing applications. "It's evolved to the point where Ingrid has created a validation methodology where a software vendor, working independently with a third party, can validate that they are in fact practicing 'Best Practices,'" Shaughnessy said.
Visa lists Software developers and specific applications on its CISP site as having successfully completed assessments. The list, dated March 24, 2005, currently names AIRCHARGE J2ME; GO Software's RITA Server; LaGarde's StoreFront; Mercantec's PowerCommerce; Radiant Systems Exhibitor and Aloha Suites; and TPI Software Smart Payment Server and Client programs. (Petitti said Ambiron conducted the compliance assessments of the solutions.)
Beierly will head up a project, similar to PCI, aimed at establishing the Payment Application Best Practices as an industry-wide initiative, not one supported only by Visa.
The New Mantra
According to Shaughnessy, establishing a highly secure system for the huge payments industry doesn't happen overnight. Instead, migrating to more stringent procedures and technologies is a gradual process; not everyone will be on board immediately.
Improved solutions are available, including sophisticated analytic tools that detect potentially fraudulent data, and "end-to-end" solutions. Ambiron and partner Mercantec, for example, developed the PCI SecureSite solution to give merchants a way to secure their transaction chain from the hosting provider to the gateway.
Noell believes that the emerging trend of consumers jumping ship, switching banks and reducing their online spending, is a reaction to a problem that will only be detrimental to the industry.
"Ultimately, this is not a very good solution, and it's one that whether through public policy or as a community, we need to avoid," he said.
As Petitti put it, "Consumers hold the key. If they stop spending, there isn't a lot for merchants, acquirers or any entity in the supply chain to do." Except to recite the new data security mantra: Don't store what you don't need.
| 








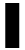 t's only April, but 2005 is already a big year for identity theft news, which seems to have reached epidemic proportions. Criminals stole data from 145,000 ChoicePoint records in October 2004, but the company didn't announce the breach until February 2005, nearly four months later, when it began to notify consumers that their information might have been compromised.
t's only April, but 2005 is already a big year for identity theft news, which seems to have reached epidemic proportions. Criminals stole data from 145,000 ChoicePoint records in October 2004, but the company didn't announce the breach until February 2005, nearly four months later, when it began to notify consumers that their information might have been compromised.


